Build a security-first culture with interactive, localized training that change behaviour
Multi-channel phishing using AI and public company data. Auto-train after clicks
Email Threats
Empower employees to flag attacks whilst AI handles triage at scale
SaaS Security
Protect business apps from misuse, shadow accounts, and risky configurations.
Breach Monitoring
Respond fast to breaches, limit damage, and prepare your team for follow-up scams.
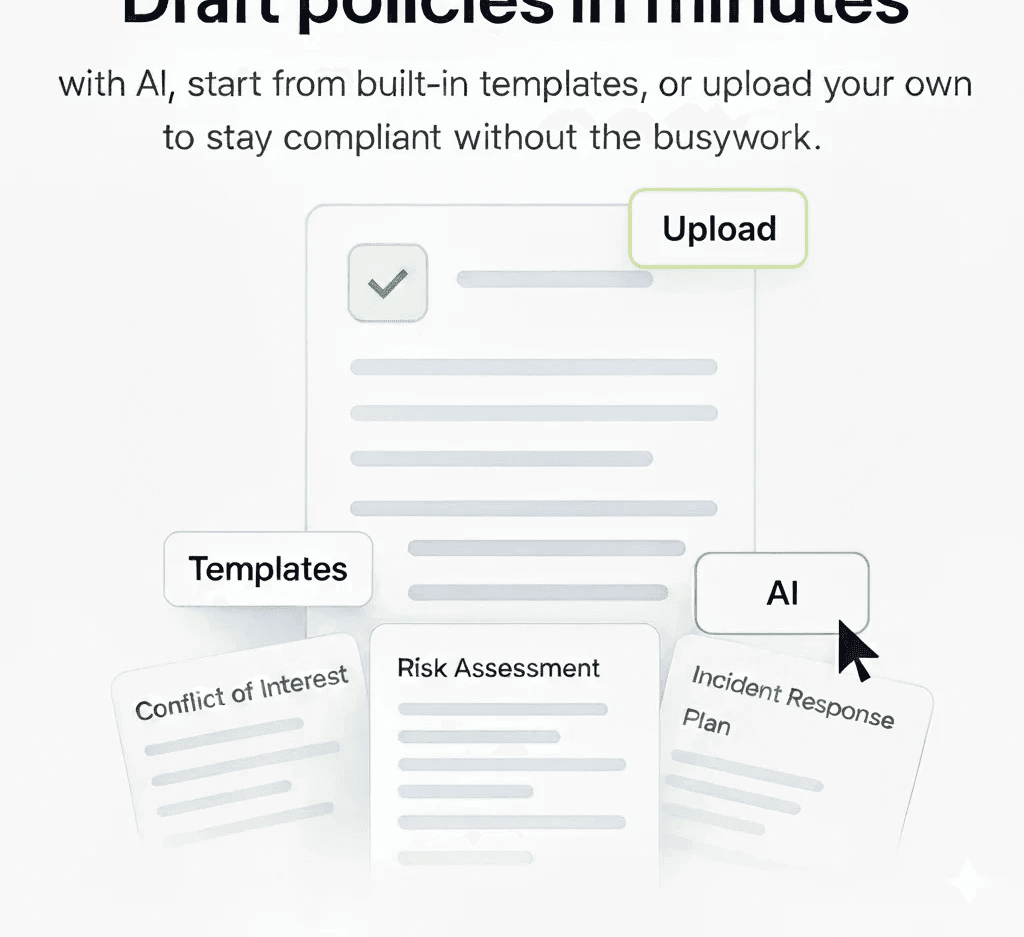
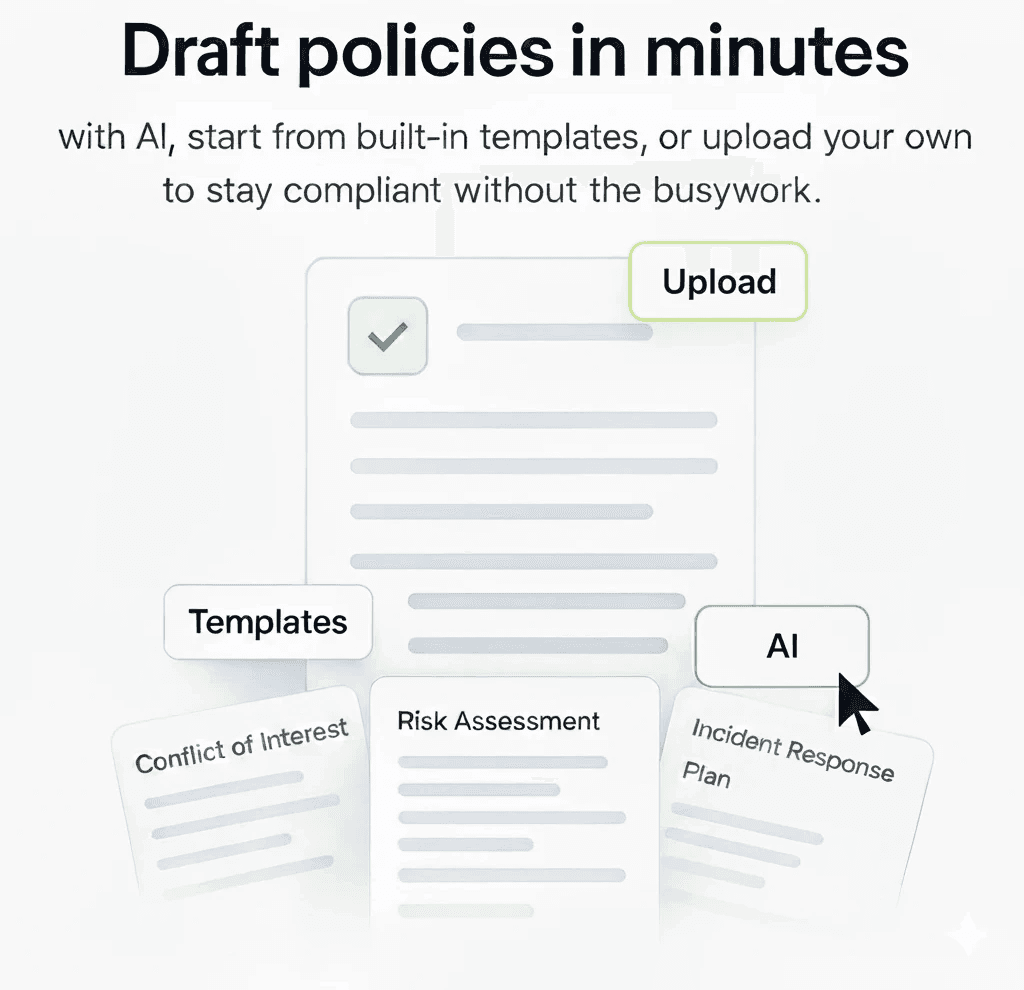
Policy & Compliance
Create, manage, and track all your security and compliance policies from one place
Integrations
Advanced Admin Toolkit
Perks as a waitlist member
Get Early bird Benefits
Obtain early access to our platform and remain informed.
Exclusive Discount
30% Off
Influence Product
Product tweaks
Trusted By Early Customers